Is the Internet of Things (IoT) truly as secure as we believe, or are we overlooking vulnerabilities that could expose our data and devices to unforeseen risks? The ability to remotely access and control IoT devices, while offering immense benefits, simultaneously introduces a complex web of potential security threats that demand our unwavering attention.
The burgeoning landscape of IoT presents an unprecedented level of connectivity, with devices communicating and exchanging data seamlessly. From smart home appliances to industrial sensors and wearable technology, these interconnected devices are transforming our lives. However, the very nature of this interconnectivity, which offers convenience and efficiency, also creates potential avenues for malicious actors to exploit vulnerabilities.
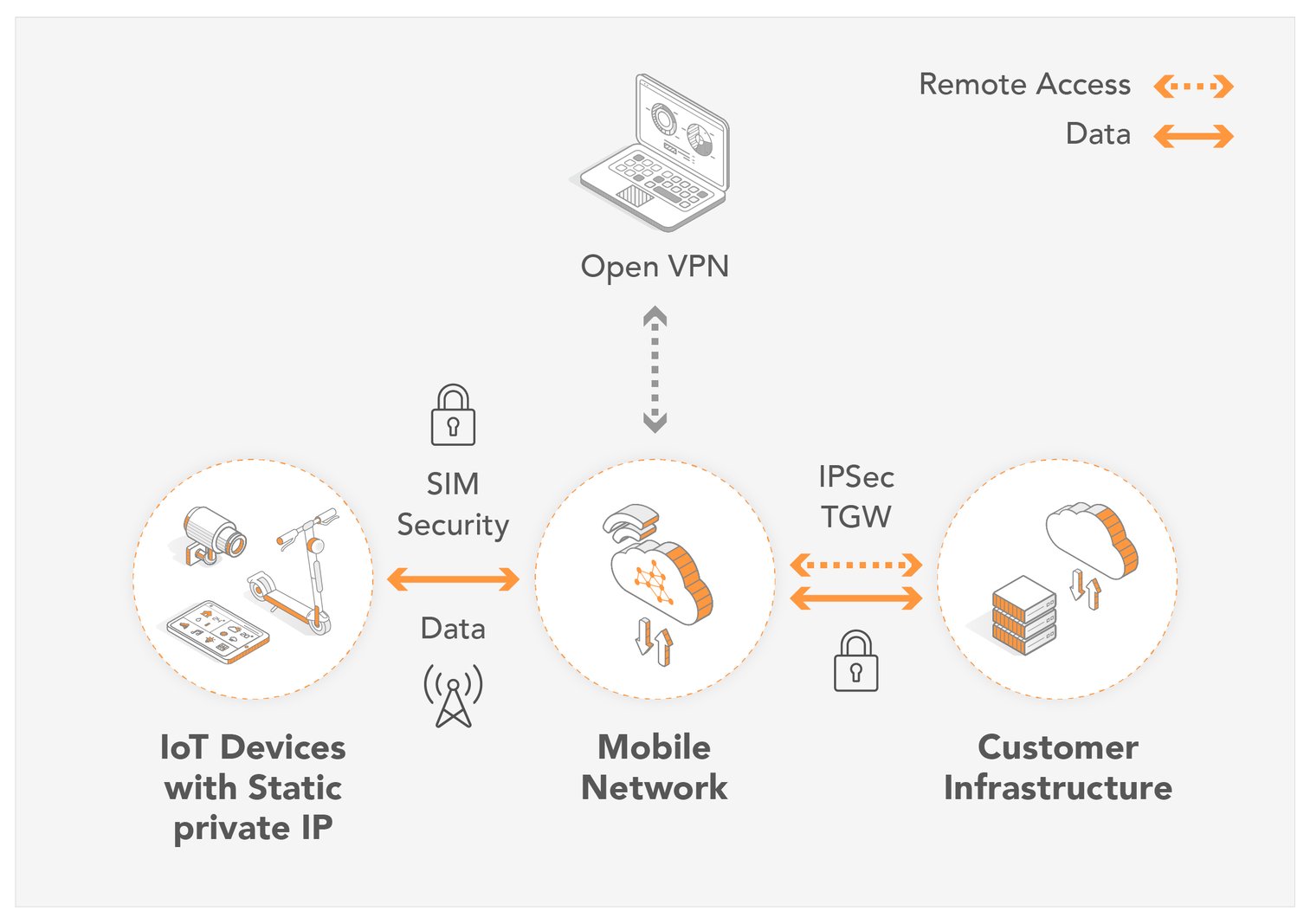
Setting up remote access for your IoT devices involves a series of steps, which may vary depending on the specific device and manufacturer. However, some general steps can provide a framework for achieving secure remote access. These steps encompass aspects such as device configuration, network setup, and the implementation of robust security measures. The goal is to establish a secure and reliable connection that enables remote monitoring, control, and management while mitigating the risk of unauthorized access.
Read also:Find Movies In Hindi Punjabi More Plus Az Movies Vega Info
The following table provides a comprehensive overview of the key aspects to consider when setting up and managing remote access for IoT devices:
| Category | Details |
|---|---|
| Device Configuration |
|
| Network Setup |
|
| Security Measures |
|
| Remote Access Methods |
|
| Device Management Platforms |
|
IoT remote access refers to the capacity to access and control an IoT device from a remote computer or device. This is achieved through various methods like SSH, VNC, and RDP, each having unique strengths, and weaknesses. However, the essential function remains the same: to provide authorized personnel the ability to interact with the IoT device from a distance.
The benefits of IoT remote access are multifaceted. Beyond the immediate benefit of being able to troubleshoot issues remotely, it provides a proactive security layer. Administrators can address unauthorized activity or potential breaches before significant damage is done. Furthermore, remote access builds upon the capabilities inherent in wireless interconnectivity, offering an extra layer of flexibility and control.
It is imperative to understand that allowing external access to your IoT devices introduces security risks. Devices that are connected to the internet are potentially vulnerable to a variety of attacks, including malware, ransomware, and distributed denial-of-service (DDoS) attacks. It's vital to implement the correct security protocols and regularly monitor activity to avoid and mitigate potential security breaches.
Many IoT devices come with default settings that may leave them open to attacks. For example, default passwords on many devices can be easily found online. In addition to being a security risk, not changing the default settings can also introduce privacy vulnerabilities. It is important to change these default settings during setup, and ideally, to customize them to fit the needs of the user. It is also important to update the software on IoT devices to patch security vulnerabilities that may be known to attackers. The software on these devices is updated frequently, so its important to stay on top of the updates. These updates can often be configured to occur automatically.
For users looking for a comprehensive solution, platforms like SocketXP provide a cloud-based IoT device management and remote access platform. This platform allows for the remote management, access, and monitoring of IoT devices, Raspberry Pi fleets, and Linux machines behind NAT routers and firewalls. SocketXP's solution works without any changes to the Wi-Fi router or firewall settings. It supports IoT Device SDKs in languages such as C and Java. This platform offers seamless and secure access to any port or service on remote IoT devices, even through closed firewalls, mobile connectivity, and across most company networks.
Read also:Kannada Movies Online Find The Best On 7movierulz In 2024 Beyond
Remote IoT, therefore, is the capability to access, monitor, and control IoT devices from a distant location. This allows for a degree of accessibility and control that would otherwise be impossible. The ability to have this sort of remote access is revolutionizing many industries, making operations more streamlined and efficient.
Upgrading to a professional or enterprise plan with many IoT management platforms offers several key advantages, including enhanced security features, improved scalability, and dedicated support. These plans offer a more robust platform to ensure the secure and efficient management of your IoT devices.
IoT device management helps businesses and consumers get the most out of their connected devices, whether it's a driverless car or a smart city. Secure access and monitoring is a necessity, whether you are a small business with a handful of devices or a large enterprise managing thousands. Platforms such as SocketXP provide business-secure access and IoT monitoring. Some platforms offer pricing models based on the number of devices being managed, with prices typically starting per device per month.
To further secure your IoT device fleet, utilize a secure IoT device management and remote access platform like SocketXP, which is trusted by thousands of customers worldwide. This platform offers a dependable solution for securely managing and remotely accessing your IoT devices.
Linux and IoT device management go hand in hand, as Linux is a popular operating system for IoT devices due to its flexibility and open-source nature. The combination of Linux and robust device management tools provides a powerful foundation for managing and securing your IoT devices. Numerous tutorials are available for accessing a device behind a firewall. One challenge is often that you can't start a direct SSH session into the device because the firewall blocks all inbound traffic. These tutorials demonstrate how to open a tunnel and use it to start an SSH session to a remote device, allowing secure access.
In essence, when setting up remote access, the goal is to create a secure tunnel through which you can interact with your IoT devices without compromising their security. This requires understanding the network environment, the security protocols, and the specific requirements of the devices in question.
To fortify your IoT devices against potential security threats, following security best practices and guidelines is essential. This includes implementing strong passwords, using multi-factor authentication where possible, and regularly updating device firmware. Furthermore, it is important to monitor device activity for suspicious behavior and be prepared to respond quickly in the event of a security breach.
The ever-evolving landscape of IoT requires constant vigilance and adaptation. While the benefits of remote access are undeniable, the security implications must always be at the forefront of your considerations. By implementing robust security measures, utilizing secure remote access methods, and staying informed about the latest threats, you can successfully harness the power of IoT while minimizing the risk of security breaches. The future of IoT relies on our ability to strike a balance between convenience and security, ensuring that the connected world remains a safe and reliable place.
To find additional information, here's a link to an external source:
SocketXP Official Website