Is it possible to effortlessly monitor and control your IoT devices, even when they're tucked away behind firewalls and NAT routers? The ability to remotely access and manage devices, regardless of their location or network configuration, is not just a convenience; it's a necessity in today's interconnected world.
The increasing deployment of IoT devices and sensors in remote locations, customer sites, and open fields necessitates secure and reliable remote access. Consider the scenario of environmental monitoring, where sensors scattered across a vast area collect crucial data. Or perhaps you're managing industrial IoT applications with critical parameters that need constant adjustment. The challenge lies in overcoming the inherent obstacles of firewalls and network address translation (NAT) that often restrict external access to these devices.
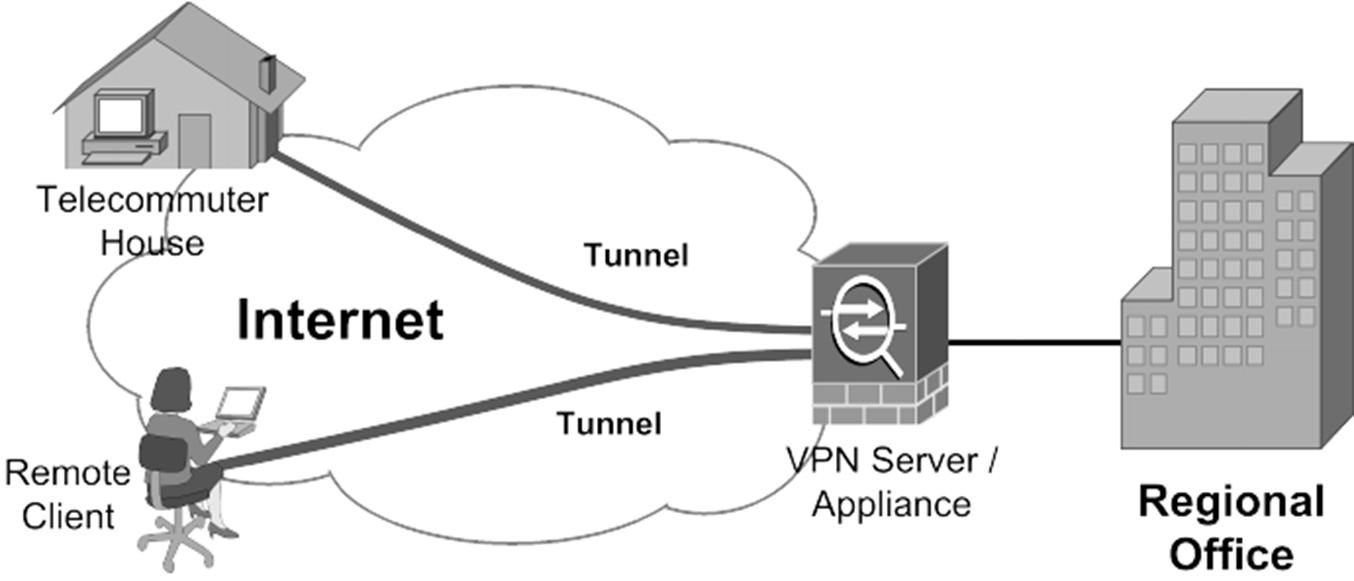
Let's delve into the intricacies of remote access solutions, exploring various techniques, tools, and best practices to ensure secure and efficient connectivity. This is especially relevant for situations where your Fortigate firewall is behind NAT, utilizing a private IP address and a higher-level device for public IP translation. While you might be able to access your firewall's web interface via the public IP, establishing a secure VPN connection using FortiClient can present its own set of challenges. We will dissect how to effectively navigate these complexities, and find the right remote access device configuration for our needs.
Read also:Missing Kannada Movies Finding Info Alternatives 20242025
The core function of a firewall, in essence, is to prevent unauthorized access to a network. While the firewall should ideally allow authorized tunnels, the specifics depend on the tunnel management approach.
Key Benefits of Secure Remote Access Solutions
Implementing a robust remote access strategy offers several key advantages, transforming how you manage and interact with your IoT infrastructure:
- Enhanced Accessibility: Gain instant access to devices regardless of their location or network configuration.
- Simplified Management: Streamline device configuration, updates, and troubleshooting from a central location.
- Improved Security: Establish secure tunnels to protect sensitive data and communications.
- Reduced Downtime: Quickly diagnose and resolve issues, minimizing disruption to operations.
- Cost Savings: Reduce the need for on-site visits and manual intervention.
The following table provides a detailed overview of common remote access methods and technologies:
| Method | Description | Pros | Cons | Use Cases |
|---|---|---|---|---|
| SSH Port Forwarding | Establishes a secure tunnel to forward traffic through an SSH connection. | Simple to set up, secure. | Requires SSH access to the device, can be cumbersome for non-technical users. | Accessing web servers or services behind a firewall. |
| VPN Solutions (IPsec, OpenVPN) | Creates a secure encrypted tunnel between your device and the remote network. | Highly secure, supports multiple protocols, versatile. | Can be complex to configure, requires compatible devices. | Connecting to entire networks, accessing internal resources. |
| Reverse SSH/SSL Tunnels (SocketXP, ngrok) | Establishes a tunnel from the internal network to an external server. | Easy to set up, bypasses firewall restrictions. | Requires a publicly accessible server or platform, security considerations. | Accessing web applications behind NAT, device management. |
| MQTT Brokers (with remote access features) | Utilizes MQTT for secure communication, often with built-in remote access capabilities. | Efficient for IoT, supports bi-directional communication, scalable. | Requires an MQTT broker, configuration can be complex. | Monitoring and controlling IoT devices, data collection. |
| Port Knocking | Sends a specific sequence of packets to temporarily open firewall ports. | Adds an extra layer of security. | Requires precise timing, can be unreliable. | Adding a layer of security to remote access. |
The success of your remote access strategy often hinges on understanding how the NAT device operates. Typically, NAT devices map internal IP addresses and source ports to a destination IP and port, limiting communication to only those pairs. This inherent restriction essentially creates a rudimentary stateful firewall, which can complicate efforts to establish seamless remote connections.
This is where more sophisticated solutions like secure tunneling using MQTT and WebSockets can offer an advantage. This approach transfers an access token to the device, using WebSockets to establish an SSH connection through the firewall, providing a secure pathway for remote access.
Creating secure reverse SSL/TLS tunnels through platforms like SocketXP is a robust method to selectively expose applications or services that run in your private network, whether behind a NAT router or a firewall, to your customers or vendors. The key benefit is a straightforward and secure approach to manage IoT devices remotely.
Read also:Is Movierulz Safe Alternatives Latest Updates Keyword Movierulz
SocketXP addresses the security concerns inherent to SSH, offering a more secure alternative. Moreover, with such platforms, you won't need to manually discover the device's IP address or modify firewall settings. You gain direct access to your Raspberry Pi, for example, via SSH or VNC, as if it were on your local network, regardless of its location.
For those seeking a less intrusive approach, consider using a simple shell script to monitor a readily available internet resource. This script would listen for commands to initiate a reverse tunnel, offering a way to maintain remote access without permanently opening ports. This approach is especially useful when frequent access is not required.
The type of firewall you choose should align with your organization's specific security needs and the level of protection needed for your remote access devices. Your security requirements and the level of protection necessary for remote access devices are key factors.
Remote access devices come in many forms, and each is designed to address particular use cases and needs. Some of the most common types include:
- VPN Gateways: VPNs create secure tunnels for remote access.
- Firewalls with Remote Access Capabilities: Firewalls can include built-in remote access features.
- IoT Gateways: These gateways are designed specifically for IoT environments.
- Remote Desktop Software: Software like TeamViewer or VNC allows direct access to a device's interface.
For active FTP, ports 20 and 21 are utilized on the server-side. If passive FTP is in play, a unique high-number port is established for each session. At this point, you would need a device that supports protocol inspection and dynamic access rules (a firewall).
While the initial setup may seem complex, the benefits are clear: efficient remote access, easier management, and improved security for your IoT devices.
Remote access to a Linux server, even when behind a firewall, is often achieved with techniques such as port knocking, P2P or VPN solutions, and SSH. Port knocking involves sending a specific sequence of packets to open a temporary hole in the firewall. P2P or VPN solutions like Hamachi handle the intricacies of firewall negotiation.
Despite careful planning, unexpected hurdles can emerge when connecting to an IoT device behind a firewall. Here are some common problems and their solutions:
- Firewall Blocking Connections: Ensure the firewall allows inbound connections on the required ports. Consider using port forwarding, VPNs, or reverse tunnels.
- NAT Issues: Understand how NAT translates IP addresses and ports. Configure port forwarding on your router or use a platform that handles NAT traversal.
- Network Connectivity Problems: Verify the IoT device has a stable internet connection. Troubleshoot network settings and connectivity issues.
- Authentication Errors: Double-check your credentials and authentication settings. Make sure the device is configured correctly.
- Incorrect IP Addresses: Ensure you have the correct IP addresses for both the IoT device and the remote access endpoint. Use dynamic DNS if the device's IP changes.
When working with a Fortigate firewall, it is essential to know how to configure IPSec remote access to achieve full tunneling. You should also be able to ping the LAN's default gateway behind the Fortigate and run route print to confirm that the internal segment is reachable via the VPN pool IP.
In the evolving landscape of IoT, setting up remote access can feel like piecing together a complex puzzle. However, with the right expertise and tools, it becomes manageable. The journey from challenges to effective solutions isn't just about following a technical guide; it's about adapting and learning.